On this page
Awesome Lists
Awesome lists are carefully curated collections of projects and resources contributed by the community. These lists cover a wide range of topics, from command-line interface applications to fantasy literature, offering something for nearly every interest.
TL;DR:
- DeepSeek AI
- Application Security
- Security
- CTF: Capture The Flag.
- Cyber Security University: Free educational resources that focus on learning by doing.
- Malware Analysis
- Android Security
- Hacking
- Hacking Spots
- Honeypots: Deception trap, designed to entice an attacker into attempting to compromise the information systems in an organization.
- Incident Response
- Vehicle Security and Car Hacking
- Web Security: Security of web apps & services.
- Lockpicking: The art of unlocking a lock by manipulating its components without the key.
- Cybersecurity Blue Team: Groups of individuals who identify security flaws in information technology systems.
- Fuzzing: Automated software testing technique that involves feeding pseudo-randomly generated input data.
- Embedded and IoT Security
- GDPR: Regulation on data protection and privacy for all individuals within the EU.
- DevSecOps: Integration of security practices into DevOps.
- Executable Packing: Packing and unpacking executable formats.
- Malware Persistence: Techniques that adversaries use to keep access to systems across restarts.
- EVM Security: Understanding the Ethereum Virtual Machine security ecosystem.
- Password Cracking: The process of recovering passwords from data that has been stored in or transmitted by a system in scrambled form.
- Security Card Games: Train your skills and discuss various security topics.
- Suricata: Intrusion detection/prevention system and network security monitoring engine.
- Prompt Injection: A type of vulnerability that specifically targets machine learning models.
- Detection Engineering: Design, build, and operate detective cybersecurity controls.
Blogs
Many security experts utilize blogs as a medium to disseminate knowledge, increase awareness, and foster the development of the cybersecurity community. Blogs serve as a vital link between technical specialists, businesses, and the public, offering insights, updates, and guidance in a format that is easy to understand.

Books
More:
Communities

Conferences




Events
CTFs
A Capture the Flag (CTF) challenge is a competitive event where participants tackle cybersecurity-related tasks to capture “flags,” which serve as digital trophies. This interactive, game-like format allows individuals and teams to hone their cybersecurity expertise, discover new methods, and enjoy the process.



Games
Artificial Intelligence

Machine Learning
Generative Pre-trained Transformer (GPT) is a more recent type of advanced artificial intelligence model developed primarily for generating and understanding human-like text. It’s like having a highly intelligent text-based assistant that can answer questions, create content, translate languages, summarize text, and more.
- Code Copilot: Code Smarter, Build Faster—With the Expertise of a 10x Programmer by Your Side.
- Cover Letter By masterinterview.ai: Boost interviews with compelling cover letters tailored to job applications—simple, quick, effective.
- Python By Maryam Eskandari: A Python assistant for all skills levels, pre-trained on python.org and stackoverflow.com.
- Python By Nicholas Barker: A highly sophisticated GPT tailored for Python programmers. Optimized for GPT-4o.
Labs


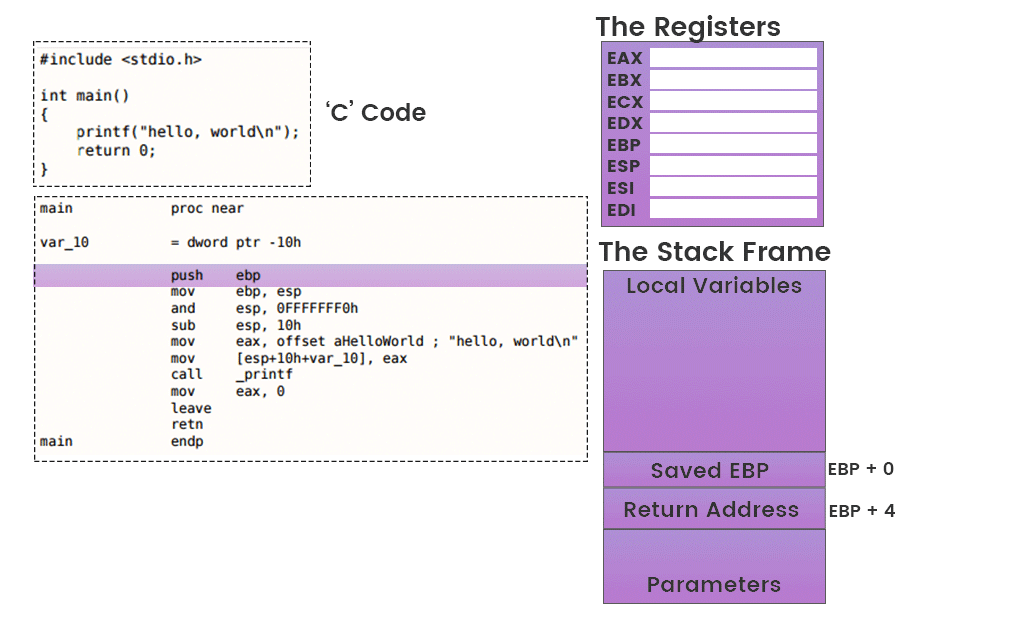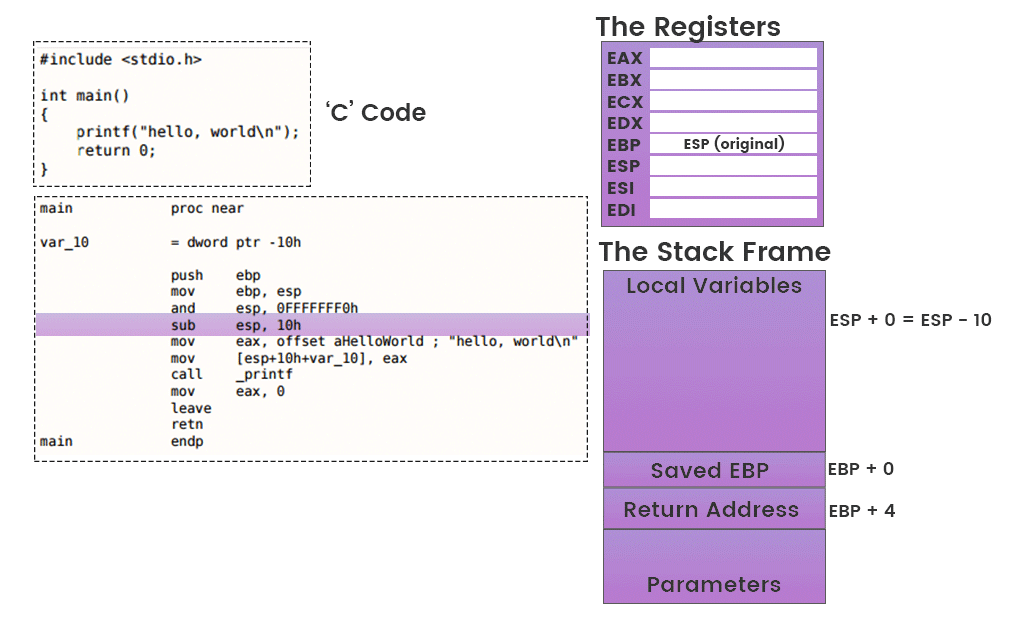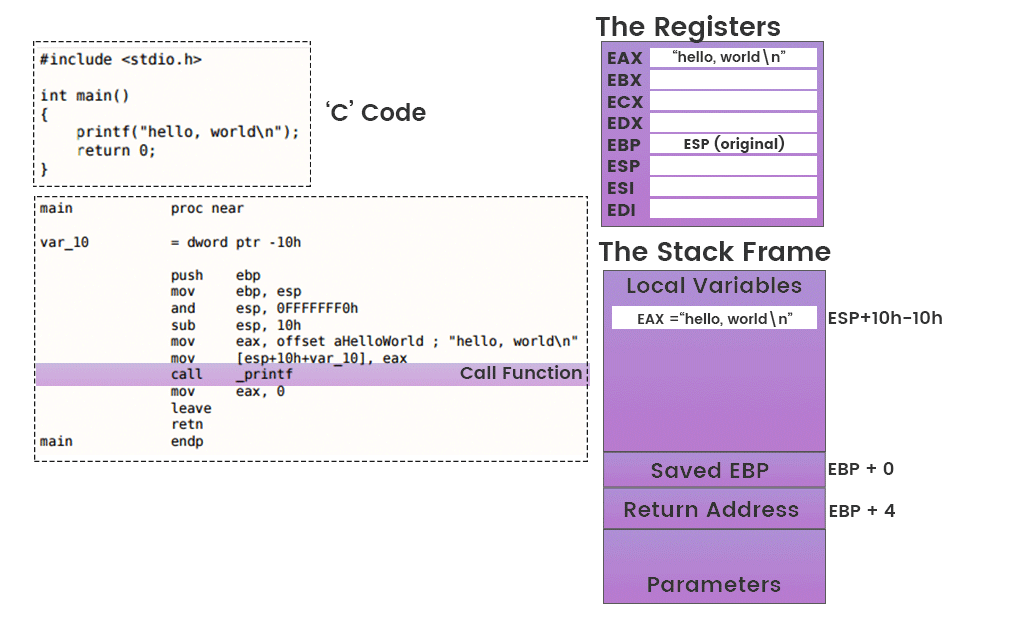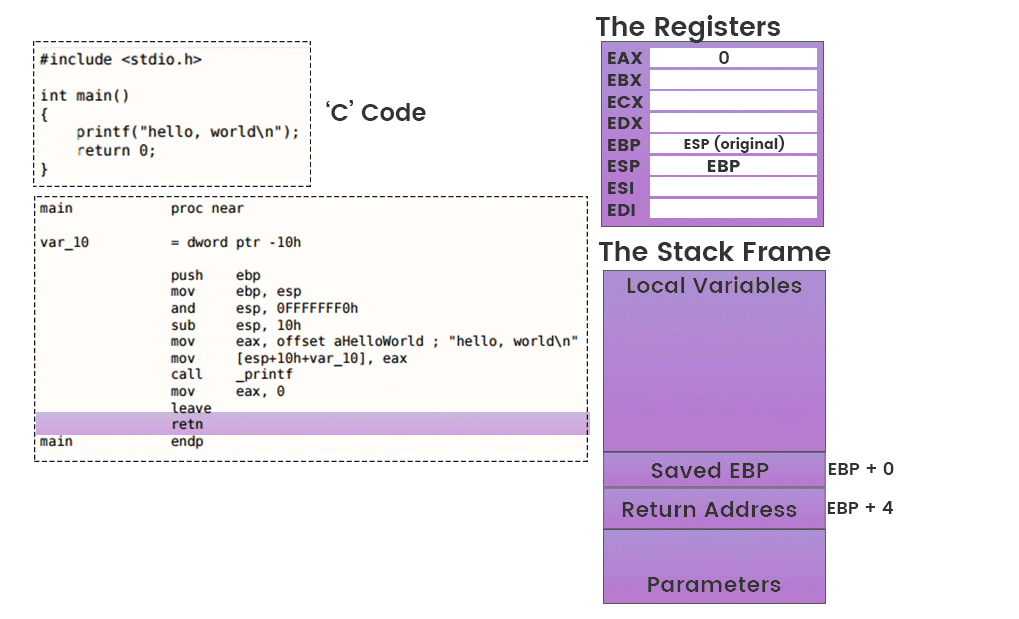

Newsletters

OffSec
Offensive Security (OffSec) is a proactive, adversarial approach to cybersecurity, focusing on identifying and exploiting flaws in systems, networks, or applications to enhance their security. The goal of offensive security is to think and act like an attacker to identify weaknesses before they can be exploited.


Programming
More:
Ranges / War Games

Research


Tools
Training





Web Application Security


Web Development
This website is built on some exceptional technologies, both open source and freemium.
Publishing Platforms

Ghost Blog Themes
Web Icons
Writeups
Writeups are a detailed technical document describing the process of solving a particular challenge, exploit, or security problem in the corporate and academic world. Writeups are typically created after solving CTF challenges, building labs, or even as lessons learned from real-world incidents. They serve as an educational resource, helping the community to understand the steps, tools, and thought processes involved in identifying and addressing vulnerabilities or solving complex technical problems.



































